OpenDOF Support and Training
Challenge us, challenge yourself!Many Support and Training Options are Available
We realize that adopting new technology can be a daunting task. Fortunately, DOF technology can rely on its maturity and flexibility to make that task easier. DOF has been used, tested, and put into production world-wide. There are many experts that are willing to help you from the ground up and we’re always improving our support. We also want to help you become one of those experts. That’s why we’ve made it easy to start, with online, or on-site training, to become an expert with DOF.
This page is a hub for many of the basic questions we hear. It is where you can get the support you need and the training (from basic to advanced) to make anyone able to adopt DOF Technology.
Complete, Self-Guided, OpenDOF Java Training Now Available!
OpenDOF Java training from beginning to end…
DOF Overview
The acronym DOF (Distributed Object Framework) refers to a technology that allows many different products, using many different standards, to work together and share information effortlessly across many different networks (e.g., LAN, WAN, Intranet, Internet—any type of network or mesh). At its core, the DOF technology was designed to network embedded devices, whether simple or complex. However, to support advanced networking functions for those devices, DOF functionality has evolved into a server technology, appropriate for services that expand the functionality of networked devices, whether those services reside on your own physical servers, or you are taking advantage of advanced cloud technology, such as Amazon Web Services. Ultimately, DOF applications have the flexibility to enhance all products, from the simplest resource-constrained device to the most powerful of computer networks.
You can see a complete overview in “The Overview of DOF Technology” (link will open a new tab at: https://slate.adobe.com/cp/vgeaY/).
The DOF Object Model
The DOF Object Model was created to help simplify implementation and programming. In essence, the Object Model consists of a few key parts.
If you’re already familiar with Object Oriented Programming (OOP), the terms that follow will sound familiar. However, there are differences between DOF Objects and objects as they are defined in OOP. Don’t worry though, it’s easy and the differences will make perfect sense.
Read our complete self-guided training on the DOF Object Model!
DOF Objects
DOF Objects are collections of functionality. This functionality is provided through DOF Interfaces. In OOP, an object is a programming element with properties and behaviors. DOF Objects are collections of functionality, and they provide this functionality through Interfaces.
DOF Objects can represent either physical or logical devices. They provide functionality, are dynamic (their capabilities can change), and are defined (which means all the capabilities of a DOF Object are discoverable). DOF Objects are referenced by an Object Identifier (OID) that is globally unique.
DOF Interfaces

DOF Interfaces are contracts through which the functionality from a DOF Object is defined. This allows you to govern an object’s capabilities and data. You create an Interface to form an “as-is” relationship with a DOF Object. DOF Interfaces require three building blocks: Items, Types, and an Interface Identifier (IID) that is globally unique.
Once an Interface has been created and approved, it is published and stored in a global Interface Repository. Why are interfaces published? Because they are often referenced and reused for many different projects. And since changing an interface has the potential to break any number of projects that use it, published interfaces do not change!
Items
Items are individual “pieces” of functionality within an Interface. These pieces, or “items of functionality,” are Properties, Methods, Events, and Exceptions. Interface Items are crucial to an Interface. Many programmers reading this will be familiar with the items of functionality already (i.e., Properties, Methods, Events and Exceptions).
What is different about interface items is the Item ID. This is an identifier that is unique within the Interface itself. For example, Item ID 1 may refer to a Property, Item ID 2 may refer to a Method, and so on. Both Item IDs will be contained within a single Interface with its own globally unique IID.
Types
Types define the data. For example, a type could be uint8, structure, string, array, float, and so on. Types are predefined for specific protocols and will define the required metadata. Application developers define the parameters for the item’s metadata (related types, lengths, arrays, etc.) and assign an identifier for each type. Each type requires a unique identifier that must be registered. However, since identifiers are built into the libraries, developers will rarely see them.
Have Questions?
DOF Operations
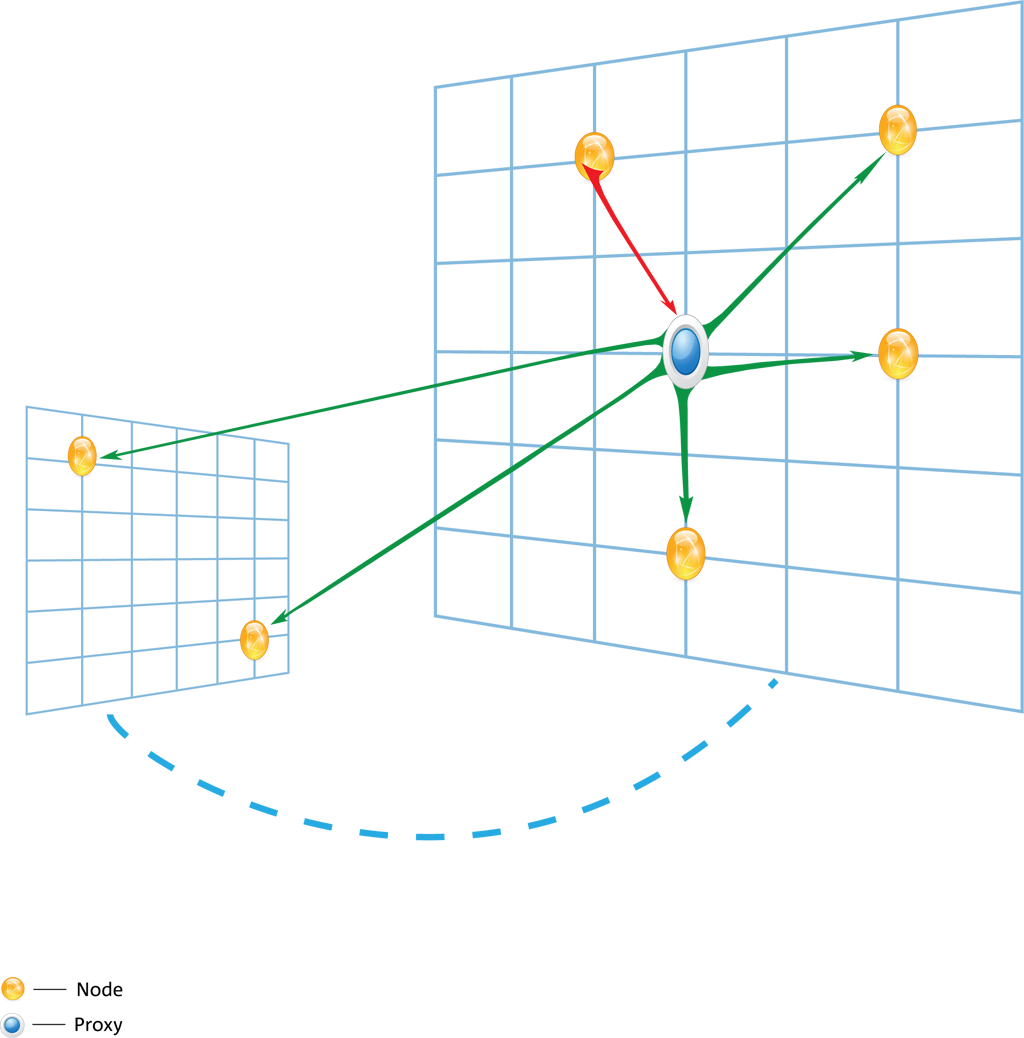
A DOF Operation is the core programming technique that allows functionality on one or more nodes. A node may be one, or a combination of, a provider, requestor, and proxy:
- Provider: these nodes provide functionality
- Requestor: these nodes request functionality from a Provider
- Proxy: these nodes forward operations and, in a network topology, lie between a Requestor and Provider. This allows them to also route operations without processing them.
Providers and Requestors can process both synchronous and asynchronous operations on properties, methods, or events in a DOF Interface.
Want to learn more? Dive into our DOF Operations Training course.
DOF Connectivity
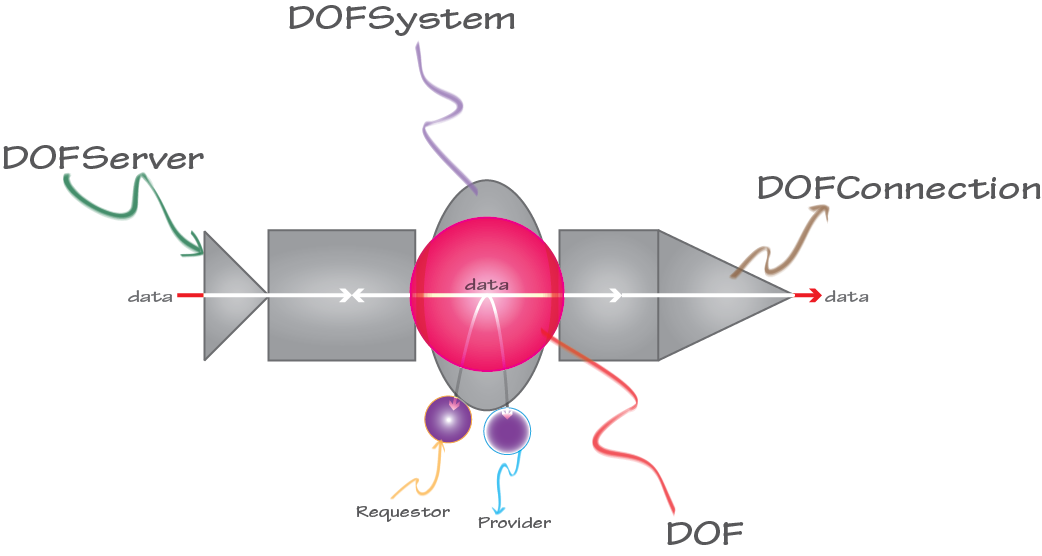
This is an illustration of DOF Connectivity. Once you instantiate a DOF, you can create a DOFSystem and then add Requestors and/or Providers. To initiate connections from your DOF, you create a DOFConnection. Creating a DOFServer allows you to accept connections from another DOF, which, in turn, allows data to transfer between them, ready to be processed by your application logic. All of these components start with DOF, which can be a single component connected to a DOF or part of a combination.
Sounds simple, right? Well, it is! Sure, there are details to consider, but we have DOF Connectivity Training to help you get started.
DOF Security
DOF Security has been integrated from the protocol layer, up. That does not mean security is done for you, it simply means that DOF Security has been integrated across the wire. You still have to design secure applications; what we have done is just made it easier for you to do more effectively. DOF Security leverages common libraries and components that are easier to understand as well as easier to manage and integrate into projects, products, and applications. Consider the following:
- Full Access Control: You control who has access and to what level. This includes resources.
- Authentication: The DSP can centralize security information, creating a shared trust environment without exposing credentials.
- Encryption and cryptography: Connections and traffic are encrypted using fully implemented, tested standards such as AES.
- Cypher technology can be switched from one standard to another. For example, AES can be switched to standards used in other countries.