
sdk-opendof-c-7-1.1 Release Announcement
The OpenDOF Project is pleased to announce the release of an updated C SDK for OpenDOF 7. The SDK is an important component for training and development of C applications using DOF Technology.
This component is a package of OpenDOF libraries, tools and support components for the C programming language.
The SDK is available on our Download page.
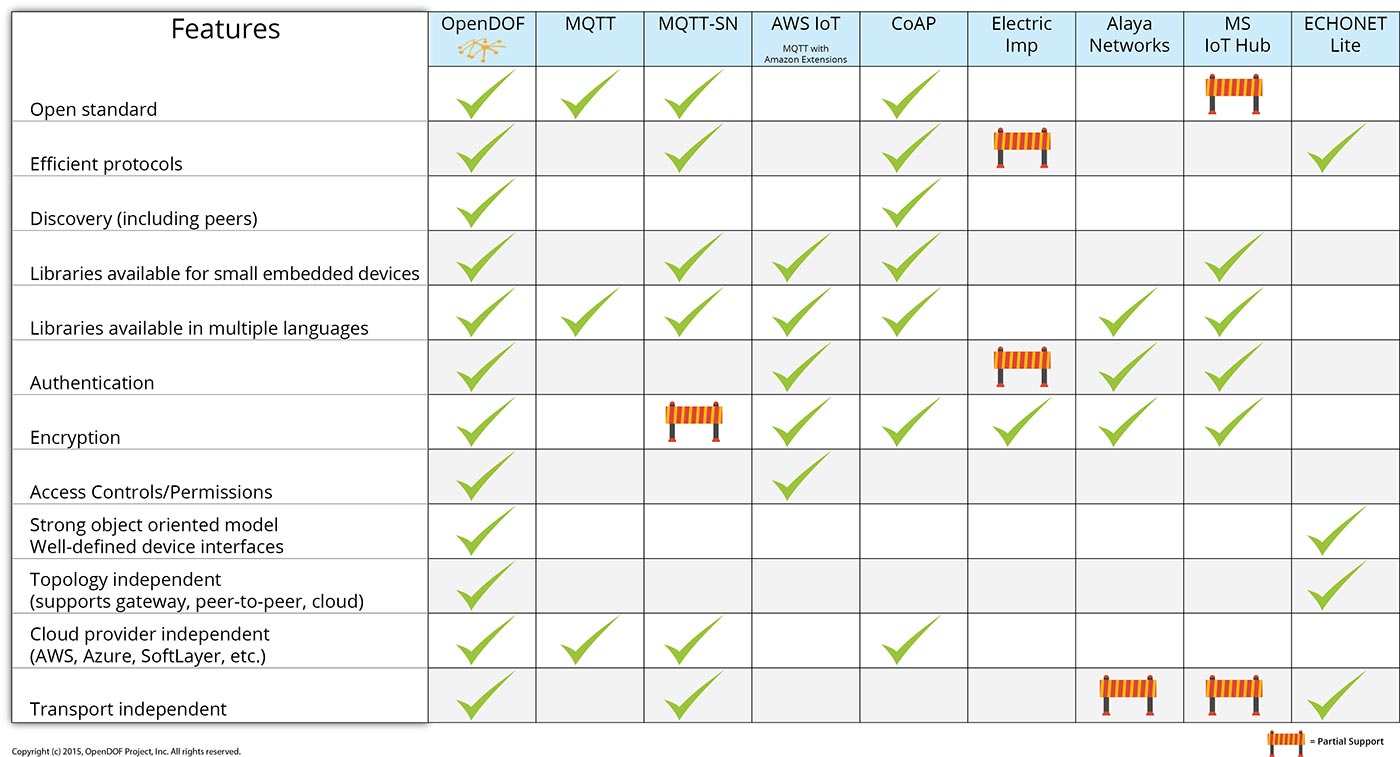
How Does OpenDOF Compare?
How Does OpenDOF Compare?
MQTT, AWS IoT, CoAP, Electric Imp, Ayla Networks, MS IoT Hub, and ECHONET Lite compared to OpenDOF
Training Introduction-An Overview of DOF Technology
We’ve found, over the years, that a brief look at the “destination” (what you will be able to accomplish) makes all of the difference. Whether you’re familiar with some of the concepts of DOF Technology or just starting, clicking on the image below will help! This presentation will give you an overview of the various components used in our Operations, Connectivity and Security training. It is high level, so you do not need to be a programmer to appreciate what is offered!
Understanding the DOF Object Model
The DOF Object Model was created to simplify the implementation and programming tasks associated with the OpenDOF Project and its Object Access Libraries (OALs). The DOF Object Model describes and defines the technological foundation of the OpenDOF Project. It shows how DOF Objects, DOF Interfaces, and other related elements work together to create scalable and reliable network services based on a system of providers and requestors in peer-to-peer relationships.
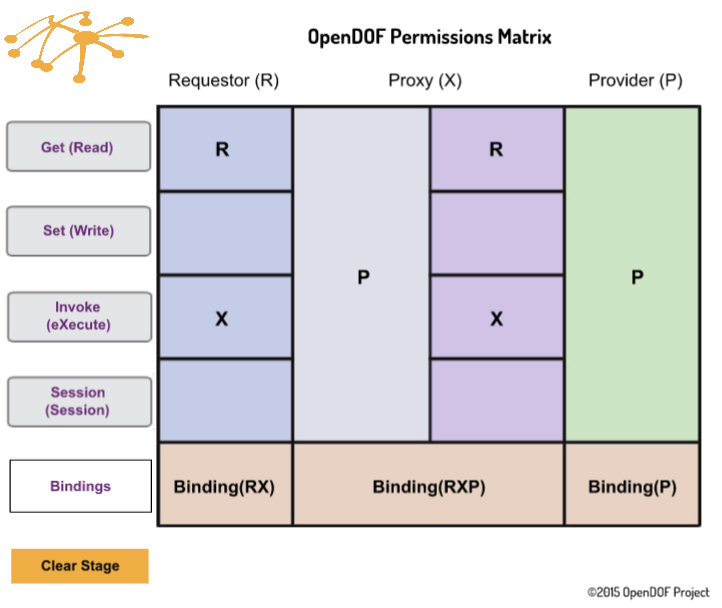
Permissions Matrix
The OpenDOF Permissions Matrix is a simple, interactive demonstration created to let you see how basic permissions work with DOF Technology.
The Matrix displays Operations and their corresponding binding: Get (Read), Set (Write), Invoke (eXecute) and Session (Session). By clicking on one of the four Operations buttons, you will see the binding displayed across a Requestor (R), Proxy (X) and Provider (P).
Along the bottom row, bindings are displayed for each object, in proper order (left to right).